Rebonjour 
J’ai échangé pas mal sur le matrix de woob et j’ai pu tester pas mal de choses. Malheureusement le problème n’est pas résolu.
Je fais une synthèse ici pour la postérité au cas où ça peut servir à d’autre (ou si finalement quelqu’un a une idée d’où le problème pourrait venir) 
Caractéristiques de mon système
- OS : Endeavour OS (arch linux) sous KDE
- Installation de kresus via le repo Archlinux : Arch Linux - kresus 0.21.2-2 (x86_64)
- Execution sur la machine directement (pas de container ou VM)
- Utilisation d’un VPN avec filtrage DNS sous NextDNS
Le problème semblerait venir effectivement d’un certificat auto-signé qui n’est pas accepté par woob.
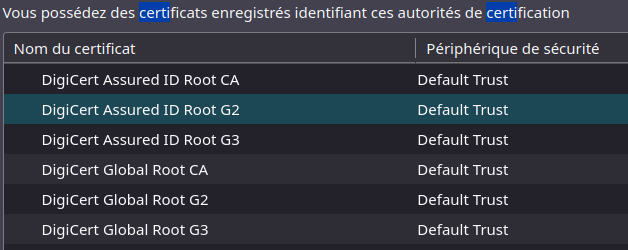
Ajout du certificat racine Digicert Root G2
- Récupération de la clé publique du certificat via
openssl s_client -connect www.credit-cooperatif.coop:443 -showcerts < /dev/null
trust anchor --store digicert-root.crt- Le certificat a bien été ajouté dans
etc/ca-certificates/trust-source/
- Test aussi de la commande
trust extract-compat
Vérifications de la chaîne de certification (hors woob)
openssl s_client -connect www.credit-cooperatif.coop:443 -showcerts < /dev/null
Résultat (fonctionne)
Connecting to 18.245.199.81
CONNECTED(00000003)
depth=2 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2
verify return:1
depth=1 C=US, O=DigiCert Inc, CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
verify return:1
depth=0 C=FR, L=PARIS, O=BPCE SA, CN=www.credit-cooperatif.coop
verify return:1
---
Certificate chain
0 s:C=FR, L=PARIS, O=BPCE SA, CN=www.credit-cooperatif.coop
i:C=US, O=DigiCert Inc, CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Aug 5 00:00:00 2024 GMT; NotAfter: Sep 5 23:59:59 2025 GMT
-----BEGIN CERTIFICATE-----
MIIG7TCCBdWgAwIBAgIQBtRT/wSQLRDi0wNw0OPa+TANBgkqhkiG9w0BAQsFADBZ
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMTMwMQYDVQQDEypE
aWdpQ2VydCBHbG9iYWwgRzIgVExTIFJTQSBTSEEyNTYgMjAyMCBDQTEwHhcNMjQw
ODA1MDAwMDAwWhcNMjUwOTA1MjM1OTU5WjBUMQswCQYDVQQGEwJGUjEOMAwGA1UE
BxMFUEFSSVMxEDAOBgNVBAoTB0JQQ0UgU0ExIzAhBgNVBAMTGnd3dy5jcmVkaXQt
Y29vcGVyYXRpZi5jb29wMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
xK94L/NUUAQwko+aPG5sOhIq7uwKRZMUu1PXNFxnFzZp0gqXpwX5Cgo+x8c3NRR9
+yOGHHgo8vO8m5AnH9z3wt6ons4T2WSCmtuBuJdccxcy6gECn1WUygy3ML7aWRY5
IopG21Z/t6vS0hbE44dOWELBRxtc3oZP7Q6ECYKc9T2X8obS1AYFV7aNSOvgZ8IO
3gMPmnUrgSVRZm0u1uTtO9nd+u1TkRXbLdIDICkEVF46flak9eBKeq6tqbm9qoYV
S8ppCnRE7vrSJs3bYm/iN0lXpQlqavxP2xwL0+MULDMp/DQzwbOa0O4C8W3V9sB0
v28dt+PCrUS0rZ0s1E+juQIDAQABo4IDtDCCA7AwHwYDVR0jBBgwFoAUdIWAwGbH
3zfez70pN6oDHb7tzRcwHQYDVR0OBBYEFGP5UZE5S4e0Rh8O+fzLIYCZwDZdMEQG
A1UdEQQ9MDuCGnd3dy5jcmVkaXQtY29vcGVyYXRpZi5jb29wgh13d3cuZXouY3Jl
ZGl0LWNvb3BlcmF0aWYuY29vcDA+BgNVHSAENzA1MDMGBmeBDAECAjApMCcGCCsG
AQUFBwIBFhtodHRwOi8vd3d3LmRpZ2ljZXJ0LmNvbS9DUFMwDgYDVR0PAQH/BAQD
AgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjCBnwYDVR0fBIGXMIGU
MEigRqBEhkJodHRwOi8vY3JsMy5kaWdpY2VydC5jb20vRGlnaUNlcnRHbG9iYWxH
MlRMU1JTQVNIQTI1NjIwMjBDQTEtMS5jcmwwSKBGoESGQmh0dHA6Ly9jcmw0LmRp
Z2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbEcyVExTUlNBU0hBMjU2MjAyMENBMS0x
LmNybDCBhwYIKwYBBQUHAQEEezB5MCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5k
aWdpY2VydC5jb20wUQYIKwYBBQUHMAKGRWh0dHA6Ly9jYWNlcnRzLmRpZ2ljZXJ0
LmNvbS9EaWdpQ2VydEdsb2JhbEcyVExTUlNBU0hBMjU2MjAyMENBMS0xLmNydDAM
BgNVHRMBAf8EAjAAMIIBfQYKKwYBBAHWeQIEAgSCAW0EggFpAWcAdgAS8U40vVNy
TIQGGcOPP3oT+Oe1YoeInG0wBYTr5YYmOgAAAZEh4CHVAAAEAwBHMEUCIQCgWDA5
ZiLqadxLDAVzjLDBuqMQAZSMgHkBuwwHS0S3CgIgWLZ8Ek9tHG+iZX1p1OtulGqE
XPbfkXLM6jXDHK/mqiAAdgB9WR4S4XgqexxhZ3xe/fjQh1wUoE6VnrkDL9kOjC55
uAAAAZEh4CGyAAAEAwBHMEUCIA60P3YpRZD6zs8NV03ODl88hsdWNlfbuyOt6MgI
S6X7AiEAtIQb91ngtjjBWjXOQ/4icspo29+noHjMeyJmUQ2fB7sAdQDm0jFjQHeM
wRBBBtdxuc7B0kD2loSG+7qHMh39HjeOUAAAAZEh4CHIAAAEAwBGMEQCICoyxiku
lBjlBA8wiiRTzI2Okc1WG9NlGqQCfjhyA0iEAiAuV2+Xux5LlWpbGNBhZ7X2/tV1
2GZj/VlF6A7+g+Ts4zANBgkqhkiG9w0BAQsFAAOCAQEARkqZNJL6Q3zqvuZEkvvR
8AYsOhRPNHtK4f9czGMLSOsdgB7kNmiFAZAS/cwRf/2oILZx/s/N6vlR2ve28yZk
9So+BNCUjPN3oetGyWOZO+rVCloqEWT4kS4oaMD0ro16ER7y8uWrDElVUB8yhk1k
tAQP+agTCU8JwF5UFvUTatztorGWf4YKHQzO43mRSmm8bMBLTFsqAVGt1f/4iqUd
7SqqUbhe2EuT6xck9MoDR82O2OVQG97ZfQHlRT6Bdqqui4KlhyVpO9Pre9Da3MB9
BbY3osTXyEOp6GViJ4/USlF0GJq63KRdEk5BT7Zrm6ll/9rpIwyXbgX3tC1l4Rbk
6Q==
-----END CERTIFICATE-----
1 s:C=US, O=DigiCert Inc, CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
i:C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Mar 30 00:00:00 2021 GMT; NotAfter: Mar 29 23:59:59 2031 GMT
-----BEGIN CERTIFICATE-----
MIIEyDCCA7CgAwIBAgIQDPW9BitWAvR6uFAsI8zwZjANBgkqhkiG9w0BAQsFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBH
MjAeFw0yMTAzMzAwMDAwMDBaFw0zMTAzMjkyMzU5NTlaMFkxCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxMzAxBgNVBAMTKkRpZ2lDZXJ0IEdsb2Jh
bCBHMiBUTFMgUlNBIFNIQTI1NiAyMDIwIENBMTCCASIwDQYJKoZIhvcNAQEBBQAD
ggEPADCCAQoCggEBAMz3EGJPprtjb+2QUlbFbSd7ehJWivH0+dbn4Y+9lavyYEEV
cNsSAPonCrVXOFt9slGTcZUOakGUWzUb+nv6u8W+JDD+Vu/E832X4xT1FE3LpxDy
FuqrIvAxIhFhaZAmunjZlx/jfWardUSVc8is/+9dCopZQ+GssjoP80j812s3wWPc
3kbW20X+fSP9kOhRBx5Ro1/tSUZUfyyIxfQTnJcVPAPooTncaQwywa8WV0yUR0J8
osicfebUTVSvQpmowQTCd5zWSOTOEeAqgJnwQ3DPP3Zr0UxJqyRewg2C/Uaoq2yT
zGJSQnWS+Jr6Xl6ysGHlHx+5fwmY6D36g39HaaECAwEAAaOCAYIwggF+MBIGA1Ud
EwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFHSFgMBmx9833s+9KTeqAx2+7c0XMB8G
A1UdIwQYMBaAFE4iVCAYlebjbuYP+vq5Eu0GF485MA4GA1UdDwEB/wQEAwIBhjAd
BgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwdgYIKwYBBQUHAQEEajBoMCQG
CCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wQAYIKwYBBQUHMAKG
NGh0dHA6Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbFJvb3RH
Mi5jcnQwQgYDVR0fBDswOTA3oDWgM4YxaHR0cDovL2NybDMuZGlnaWNlcnQuY29t
L0RpZ2lDZXJ0R2xvYmFsUm9vdEcyLmNybDA9BgNVHSAENjA0MAsGCWCGSAGG/WwC
ATAHBgVngQwBATAIBgZngQwBAgEwCAYGZ4EMAQICMAgGBmeBDAECAzANBgkqhkiG
9w0BAQsFAAOCAQEAkPFwyyiXaZd8dP3A+iZ7U6utzWX9upwGnIrXWkOH7U1MVl+t
wcW1BSAuWdH/SvWgKtiwla3JLko716f2b4gp/DA/JIS7w7d7kwcsr4drdjPtAFVS
slme5LnQ89/nD/7d+MS5EHKBCQRfz5eeLjJ1js+aWNJXMX43AYGyZm0pGrFmCW3R
bpD0ufovARTFXFZkAdl9h6g4U5+LXUZtXMYnhIHUfoyMo5tS58aI7Dd8KvvwVVo4
chDYABPPTHPbqjc1qCmBaZx2vN4Ye5DUys/vZwP9BFohFrH/6j/f3IL16/RZkiMN
JCqVJUzKoZHm1Lesh3Sz8W2jmdv51b2EQJ8HmA==
-----END CERTIFICATE-----
2 s:C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2
i:C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Aug 1 12:00:00 2013 GMT; NotAfter: Jan 15 12:00:00 2038 GMT
-----BEGIN CERTIFICATE-----
MIIDjjCCAnagAwIBAgIQAzrx5qcRqaC7KGSxHQn65TANBgkqhkiG9w0BAQsFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBH
MjAeFw0xMzA4MDExMjAwMDBaFw0zODAxMTUxMjAwMDBaMGExCzAJBgNVBAYTAlVT
MRUwEwYDVQQKEwxEaWdpQ2VydCBJbmMxGTAXBgNVBAsTEHd3dy5kaWdpY2VydC5j
b20xIDAeBgNVBAMTF0RpZ2lDZXJ0IEdsb2JhbCBSb290IEcyMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuzfNNNx7a8myaJCtSnX/RrohCgiN9RlUyfuI
2/Ou8jqJkTx65qsGGmvPrC3oXgkkRLpimn7Wo6h+4FR1IAWsULecYxpsMNzaHxmx
1x7e/dfgy5SDN67sH0NO3Xss0r0upS/kqbitOtSZpLYl6ZtrAGCSYP9PIUkY92eQ
q2EGnI/yuum06ZIya7XzV+hdG82MHauVBJVJ8zUtluNJbd134/tJS7SsVQepj5Wz
tCO7TG1F8PapspUwtP1MVYwnSlcUfIKdzXOS0xZKBgyMUNGPHgm+F6HmIcr9g+UQ
vIOlCsRnKPZzFBQ9RnbDhxSJITRNrw9FDKZJobq7nMWxM4MphQIDAQABo0IwQDAP
BgNVHRMBAf8EBTADAQH/MA4GA1UdDwEB/wQEAwIBhjAdBgNVHQ4EFgQUTiJUIBiV
5uNu5g/6+rkS7QYXjzkwDQYJKoZIhvcNAQELBQADggEBAGBnKJRvDkhj6zHd6mcY
1Yl9PMWLSn/pvtsrF9+wX3N3KjITOYFnQoQj8kVnNeyIv/iPsGEMNKSuIEyExtv4
NeF22d+mQrvHRAiGfzZ0JFrabA0UWTW98kndth/Jsw1HKj2ZL7tcu7XUIOGZX1NG
Fdtom/DzMNU+MeKNhJ7jitralj41E6Vf8PlwUHBHQRFXGU7Aj64GxJUTFy8bJZ91
8rGOmaFvE7FBcf6IKshPECBV1/MUReXgRPTqh5Uykw7+U0b6LJ3/iyK5S9kJRaTe
pLiaWN0bfVKfjllDiIGknibVb63dDcY3fe0Dkhvld1927jyNxF1WW6LZZm6zNTfl
MrY=
-----END CERTIFICATE-----
---
Server certificate
subject=C=FR, L=PARIS, O=BPCE SA, CN=www.credit-cooperatif.coop
issuer=C=US, O=DigiCert Inc, CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 4473 bytes and written 401 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_128_GCM_SHA256
Protocol: TLSv1.3
Server public key is 2048 bit
This TLS version forbids renegotiation.
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
DONE
curl -v https://www.credit-cooperatif.coop
Résultat (fonctionne)
* Host www.credit-cooperatif.coop:443 was resolved.
* IPv6: 2600:9000:2664:8c00:7:381f:61c0:93a1, 2600:9000:2664:da00:7:381f:61c0:93a1, 2600:9000:2664:ac00:7:381f:61c0:93a1, 2600:9000:2664:7200:7:381f:61c0:93a1, 2600:9000:2664:a000:7:381f:61c0:93a1, 2600:9000:2664:ea00:7:381f:61c0:93a1, 2600:9000:2664:1200:7:381f:61c0:93a1, 2600:9000:2664:d200:7:381f:61c0:93a1
* IPv4: 18.245.199.103, 18.245.199.29, 18.245.199.36, 18.245.199.81
* Trying [2600:9000:2664:8c00:7:381f:61c0:93a1]:443...
* ALPN: curl offers h2,http/1.1
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: none
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_128_GCM_SHA256 / x25519 / RSASSA-PSS
* ALPN: server accepted h2
* Server certificate:
* subject: C=FR; L=PARIS; O=BPCE SA; CN=www.credit-cooperatif.coop
* start date: Aug 5 00:00:00 2024 GMT
* expire date: Sep 5 23:59:59 2025 GMT
* subjectAltName: host "www.credit-cooperatif.coop" matched cert's "www.credit-cooperatif.coop"
* issuer: C=US; O=DigiCert Inc; CN=DigiCert Global G2 TLS RSA SHA256 2020 CA1
* SSL certificate verify ok.
* Certificate level 0: Public key type RSA (2048/112 Bits/secBits), signed using sha256WithRSAEncryption
* Certificate level 1: Public key type RSA (2048/112 Bits/secBits), signed using sha256WithRSAEncryption
* Certificate level 2: Public key type RSA (2048/112 Bits/secBits), signed using sha256WithRSAEncryption
* Connected to www.credit-cooperatif.coop (2600:9000:2664:8c00:7:381f:61c0:93a1) port 443
* using HTTP/2
* [HTTP/2] [1] OPENED stream for https://www.credit-cooperatif.coop/
* [HTTP/2] [1] [:method: GET]
* [HTTP/2] [1] [:scheme: https]
* [HTTP/2] [1] [:authority: www.credit-cooperatif.coop]
* [HTTP/2] [1] [:path: /]
* [HTTP/2] [1] [user-agent: curl/8.11.1]
* [HTTP/2] [1] [accept: */*]
> GET / HTTP/2
> Host: www.credit-cooperatif.coop
> User-Agent: curl/8.11.1
> Accept: */*
>
* Request completely sent off
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
< HTTP/2 200
strace -f -e openat python3 -c 'import requests; requests.get("https://www.credit-cooperatif.coop/")' 2>&1 | grep cert
Résultat (fonctionne)
openat(AT_FDCWD, "/usr/lib/python3.13/site-packages/requests/__pycache__/certs.cpython-313.pyc", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/usr/lib/python3.13/site-packages/requests/certs.py", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/etc/ssl/certs/ca-certificates.crt", O_RDONLY) = 3
- Vérification du contenu du fichier
/etc/ssl/certs/ca-certificates.crt
On retrouve bien le certificat que l’on cherche (Digicert Root G2)
python3 -c 'import requests; print(requests.get("https://www.credit-cooperatif.coop/"))'
Résultat (fonctionne)
<Response [200]>
Donc a priori tout est fonctionnel est en ordre au niveau du système.
Au niveau de woob
strace -e open,openat woob bank -b creditcooperatif list 2>&1 | grep cert
Résultat (erreur)
openat(AT_FDCWD, "/usr/lib/python3.13/site-packages/requests/__pycache__/certs.cpython-313.pyc", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/usr/lib/python3.13/site-packages/requests/certs.py", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/etc/ssl/certs/ca-certificates.crt", O_RDONLY) = 3
[creditcooperatif] Identifiant client (hidden input):
[creditcooperatif] Mot de passe (hidden input):
2025-01-29 19:26:52,865:WARNING:urllib3.connectionpool:3.7:connectionpool.py:868:urlopen Retrying (Retry(total=1, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1018)'))': /se-connecter/sso?service=dei
2025-01-29 19:26:57,926:WARNING:urllib3.connectionpool:3.7:connectionpool.py:868:urlopen Retrying (Retry(total=0, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1018)'))': /se-connecter/sso?service=dei
Bug(creditcooperatif): HTTPSConnectionPool(host='www.credit-cooperatif.coop', port=443): Max retries exceeded with url: /se-connecter/sso?service=dei (Caused by SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1018)')))
Autre
Pour répondre à ta dernière question :
sudo ls -l /etc/ssl/certs/ | grep DigiCert
Résumé
lrwxrwxrwx 1 root root 76 29 janv. 16:52 244b5494.0 -> ../../ca-certificates/extracted/cadir/DigiCert_High_Assurance_EV_Root_CA.pem
lrwxrwxrwx 1 root root 71 29 janv. 16:52 252252d2.0 -> ../../ca-certificates/extracted/cadir/DigiCert_TLS_ECC_P384_Root_G5.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 3513523f.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_CA.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 399e7759.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_CA.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 607986c7.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_G2.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 69105f4f.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_CA.pem
lrwxrwxrwx 1 root root 66 29 janv. 16:52 75d1b2ed.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Trusted_Root_G4.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 7f3d5d1d.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_G3.pem
lrwxrwxrwx 1 root root 76 29 janv. 16:52 81b9768f.0 -> ../../ca-certificates/extracted/cadir/DigiCert_High_Assurance_EV_Root_CA.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 8d6437c3.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_G2.pem
lrwxrwxrwx 1 root root 71 29 janv. 16:52 9846683b.0 -> ../../ca-certificates/extracted/cadir/DigiCert_TLS_ECC_P384_Root_G5.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 9d04f354.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_G2.pem
lrwxrwxrwx 1 root root 66 29 janv. 16:52 a2c66da8.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Trusted_Root_G4.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 b1159c4c.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_CA.pem
lrwxrwxrwx 1 root root 70 29 janv. 16:52 c44cc0c0.0 -> ../../ca-certificates/extracted/cadir/DigiCert_TLS_RSA4096_Root_G5.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 c491639e.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_G3.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 c90bc37d.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_G2.pem
lrwxrwxrwx 1 root root 70 29 janv. 16:52 d52c538d.0 -> ../../ca-certificates/extracted/cadir/DigiCert_TLS_RSA4096_Root_G5.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 dd8e9d41.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_G3.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 DigiCert_Assured_ID_Root_CA.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_CA.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 DigiCert_Assured_ID_Root_G2.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_G2.pem
lrwxrwxrwx 1 root root 69 29 janv. 16:52 DigiCert_Assured_ID_Root_G3.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Assured_ID_Root_G3.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 DigiCert_Global_Root_CA.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_CA.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 DigiCert_Global_Root_G2.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_G2.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 DigiCert_Global_Root_G3.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_G3.pem
lrwxrwxrwx 1 root root 76 29 janv. 16:52 DigiCert_High_Assurance_EV_Root_CA.pem -> ../../ca-certificates/extracted/cadir/DigiCert_High_Assurance_EV_Root_CA.pem
lrwxrwxrwx 1 root root 71 29 janv. 16:52 DigiCert_TLS_ECC_P384_Root_G5.pem -> ../../ca-certificates/extracted/cadir/DigiCert_TLS_ECC_P384_Root_G5.pem
lrwxrwxrwx 1 root root 70 29 janv. 16:52 DigiCert_TLS_RSA4096_Root_G5.pem -> ../../ca-certificates/extracted/cadir/DigiCert_TLS_RSA4096_Root_G5.pem
lrwxrwxrwx 1 root root 66 29 janv. 16:52 DigiCert_Trusted_Root_G4.pem -> ../../ca-certificates/extracted/cadir/DigiCert_Trusted_Root_G4.pem
lrwxrwxrwx 1 root root 65 29 janv. 16:52 ed39abd0.0 -> ../../ca-certificates/extracted/cadir/DigiCert_Global_Root_G3.pem
Voila donc en synthèse, ça semble bloquer au niveau de woob, mais on n’a plus trop de piste.
C’est probablement lié à mon installation vu que ça fonctionne chez d’autres.
Sur archlinux le paquet kresus a pour dépendance python-requests qui lui même a pour dépendance ca-certificates alors que woob utiliserait plutôt python-certifi (mais probablement que ça n’a pas d’impact).
Merci pour tous ceux qui m’ont aidé à investiguer, j’ai essayé de retranscrire du meilleur de ma compréhension.